Click here to buy secure, speedy, and reliable Web hosting, Cloud hosting, Agency hosting, VPS hosting, Website builder, Business email, Reach email marketing at 20% discount from our Gold Partner Hostinger You can also read 12 Top Reasons to Choose Hostinger’s Best Web Hosting
Microsoft SharePoint vulnerability CVE‑2025‑53770 is more than a patch note—it’s a ticking time bomb for on‑premises servers exposed to the internet. When threat actors exploit this flaw to drop web shells and harvest machine keys, entire infrastructures can be compromised within hours. That fear is real: multiple Fortune 500 companies still run unprotected SharePoint farms, and nation‑state groups have already struck. In this article, you’ll discover why quick patching alone won’t cut it, what extra steps like key rotation you need, and how to build a layered defense that disrupts today’s attacks.
7 Game‑Changing Tips to Get the Most Out of Windows 11
Summary
| CVE ID | CVE-2025-53770 |
|---|---|
| Severity | Critical (CVSS: 8.8) |
| Affected Systems | Microsoft SharePoint Server (on-prem) |
| Type | Remote Code Execution (RCE) |
| Exploited In Wild | Yes (confirmed) |
| First Detected | July 2025 |
| Patch Released | July 9, 2025 |
What Is CVE-2025-53770?
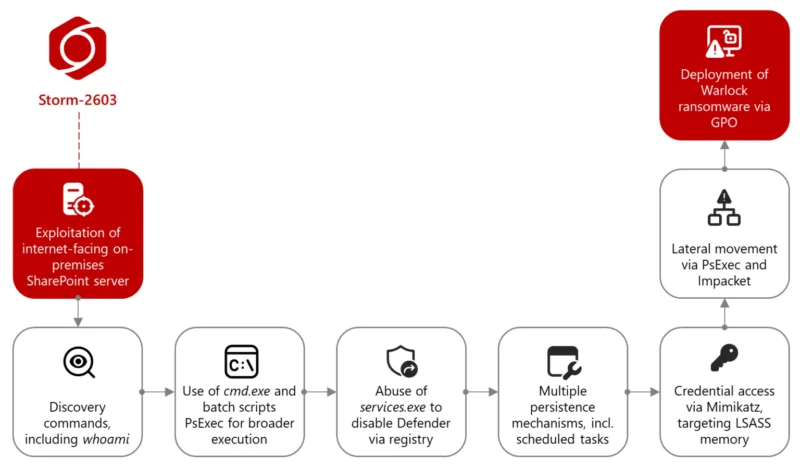
CVE-2025-53770 is a critical remote code execution (RCE) vulnerability affecting Microsoft SharePoint Server instances that are exposed to the internet. It allows unauthenticated attackers to exploit the system using crafted requests to drop web shells and execute arbitrary commands on the server.
Microsoft rated it as Critical with a CVSS score of 8.8, and multiple security vendors have confirmed its active exploitation in the wild.
Microsoft Rolls Out Windows 11 Build 27898 with Self‑Healing Recovery and Battery‑Saving Upgrades
Why This Vulnerability Demands Immediate Action
Let’s break down why this is not a typical “patch-and-forget” vulnerability:
- Exposed by default: Many organizations still have SharePoint endpoints publicly accessible.
- Easy exploitation path: Threat actors can exploit this without needing to authenticate.
- Web shells are just the beginning: Attackers are not just dropping malware—they’re harvesting cryptographic keys and laying groundwork for lateral movement.
- Nation-state interest: This vulnerability has been linked to advanced persistent threat (APT) groups with strong interest in governmental and enterprise networks.
How to Know if SharePoint Is Vulnerable
Organizations wondering how to know if SharePoint is vulnerable should:
- Check if your SharePoint servers are internet-facing.
- Verify your SharePoint build version against Microsoft’s patch documentation.
- Look for unusual network activity targeting SharePoint paths (e.g.,
/layouts/15/). - Run vulnerability scans using tools like Nessus, Qualys, or Microsoft Defender for Endpoint.
If you’re unsure, assume exposure and begin incident response steps immediately.
Microsoft Teams Add Agents and Bots in Current Conversations for Seamless AI Integration
Step-by-Step: What You Must Do (Beyond Patching)
Patching is necessary, but not enough. Here’s a layered mitigation roadmap:
1. Patch Immediately
- Apply the July 2025 cumulative update from Microsoft.
- Restart servers and ensure updates were successfully applied.
2. Audit Exposure
- Identify all SharePoint endpoints accessible from the internet.
- Block external access if not explicitly required.
- Use tools like Shodan to simulate how your infrastructure looks from an attacker’s POV.
3. Search for Web Shells
- Examine SharePoint content directories and
inetpubfolders. - Look for suspicious
.aspx,.cshtml, or obfuscated scripts. - Common paths:
\Program Files\Common Files\Microsoft Shared\Web Server Extensions\
4. Rotate MachineKeys
- SharePoint uses the MachineKey element in
web.configfor encryption and authentication. - If compromised, attackers can create valid session tokens and impersonate users.
- Rotate keys for all SharePoint sites and re-establish trust manually.
5. Update Antivirus Signatures
- Make sure Microsoft Defender or your endpoint protection is updated.
- Several threat actors drop payloads not yet flagged by default AV rules.
6. Hunt & Monitor
To answer how to know if SharePoint is vulnerable, start by hunting for key indicators such as suspicious file uploads, privilege escalation attempts, or unusual endpoint access.
- Review IIS logs for unusual POST requests or payload-like behavior.
- Enable auditing for SharePoint Admin actions.
- Correlate logs in your SIEM for anomalies across AD, Exchange, and SharePoint.
What is Windows App and Why Microsoft Replaces Legacy Remote Desktop App with this New Tool
Lessons from Past Exploits
This isn’t Microsoft’s first rodeo with SharePoint vulnerabilities:
- CVE-2020-1147 was similarly exploited by ransomware operators.
- CVE-2023-29357 allowed privilege escalation through token forgery.
Both were exploited months after patches were released—largely because orgs didn’t patch or rotate tokens.
Recommended Tools
Here are tools to help you assess and monitor your SharePoint environment:
- Microsoft Safety Scanner – https://docs.microsoft.com/en-us/windows/security/threat-protection/intelligence/safety-scanner-download
- Sysinternals Suite (Autoruns, Process Monitor) – https://docs.microsoft.com/en-us/sysinternals/
- YARA rules for detecting known web shells
- SharePoint Health Analyzer
- Shodan to check for internet exposure
FAQs
Q: Is this vulnerability being actively exploited?
Yes. Microsoft and multiple security researchers have confirmed exploitation in the wild.
Q: How to know if SharePoint is vulnerable?
You can check if your SharePoint is vulnerable by reviewing your SharePoint build number, verifying if it’s exposed to the internet, and scanning for known CVEs like CVE-2025-53770 using tools like Nessus, Microsoft Defender, or your preferred vulnerability scanner.
Q: What if my server was already compromised?
Immediately isolate the system, rotate all keys, and begin full incident response and forensic investigation. Assume lateral movement.
Q: Can cloud-based SharePoint be affected?
No. This vulnerability affects on-premises SharePoint servers only.
Microsoft Turns 50: How a Garage Startup Rewrote the Rules of Tech (and What’s Next)
Final Thoughts
This is not just another Microsoft patch Tuesday issue. CVE‑2025‑53770 shows how attackers pivot from web shells to total control within minutes. If your SharePoint is public-facing and unpatched, you’re already a target. Don’t just patch—rotate keys, hunt for threats, and lock it down. For more Windows Insider news and deep dives, subscribe to SmashingApps.com.
And if you’re asking “how to know if SharePoint is vulnerable,” the time to find out was yesterday. The time to act is now.
Click here to learn more :
- Preventing Ransomware: Ransomware Defense Checklist
Now loading...






