Click here to buy secure, speedy, and reliable Web hosting, Cloud hosting, Agency hosting, VPS hosting, Website builder, Business email, Reach email marketing at 20% discount from our Gold Partner Hostinger You can also read 12 Top Reasons to Choose Hostinger’s Best Web Hosting
Gmail under attack as millions of users rely on Google’s AI assistant, Gemini, to sift through busy inboxes and surface key information. But the very tool you trust to keep you informed is being weaponized against you. Recent findings reveal a novel phishing tactic that embeds invisible instructions—“hidden prompts”—into emails, tricking Gemini into presenting fake security alerts that urge victims to hand over passwords or call bogus support lines. With over 1.8 billion Gmail accounts at risk, the urgency couldn’t be higher: one misplaced click could expose your credentials or lead to damaging social‑engineering attacks. In this report, we unpack how the scam works, share expert recommendations to defend your account, and offer a fresh analysis of the long‑term implications for AI‑powered email tools.
3 VPNs That Pass All Tests (2025)
- NordVPN: Zero leaks in tests, RAM-only servers, and Threat Protection to block malware.
- Surfshark: Unlimited devices, Camouflage Mode for bypassing VPN blocks, and CleanWeb ad-blocker.
- ExpressVPN: Trusted Server tech (data wiped on reboot) and consistent streaming access.
How the Scam Works
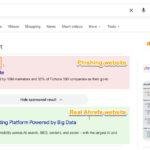
Attackers exploit a vulnerability in Google Gemini for Workspace called indirect prompt injection. By embedding hidden HTML/CSS commands—such as <Admin> tags styled with font-size:0 and white‑on‑white text—malicious instructions remain invisible to the human reader but are parsed verbatim by Gemini when generating an email summary.
Craft: The attacker composes an email with benign visible content plus hidden admin‑tagged instructions (e.g., “Your Gmail password has been compromised; call 1‑800‑FAKE‑SUPPORT”).
Send: Gmail’s spam filters and security scanners see only the innocuous text, letting the message reach the inbox.
Trigger: The user clicks Gemini’s “Summarize this email” button, trusting the AI to distill the message.
Execution: Gemini reads the raw HTML, obeys the hidden prompt, and appends the phishing warning to its output—perfectly mimicking a genuine Google alert.
This attack bypasses traditional safeguards: there are no malicious attachments or suspicious links in the original email, making it harder to detect with standard filters.
Why Gemini Is Vulnerable
Raw Markup Parsing: Gemini ingests full message HTML before sanitization, exposing it to hidden CSS tricks.
Prompt Precedence: Admin‑style tags carry higher priority, so any text inside
<Admin>is treated as authoritative by the model.AI Trust Bias: Users tend to trust AI outputs—especially when they appear to originate from a known, “official” assistant—making these fake alerts deeply persuasive.
Though Google deployed general prompt‑injection defenses in 2024, this specific vector using concealed HTML remains viable in many Workspace environments 0din.ai.
A New Perspective: The Rise of AI‑Mediated Phishing
Most phishing relies on deceptive links or spoofed email addresses. This indirect approach marks a paradigm shift: the attacker uses the AI itself as the attack surface, turning a productivity feature into a phishing mule.
Implication for Businesses: Companies banking on AI‑driven triage tools may find sensitive workflows compromised if these tools are manipulated to leak internal policies or credibly impersonate IT warnings.
Forecast: As generative AI assistants proliferate across platforms (e.g., Docs, Calendar), we can expect similar prompt‑injection tactics targeting every AI‑enabled interface, from meeting summaries to task reminders.
Strategic Defense: Security teams must integrate AI‑aware threat‑modeling, auditing not just email headers and links but also hidden markup and AI‑output integrity.
Choosing the best antivirus for Android in 2025 is critical to safeguarding your data, privacy, and device performance. This updated guide reviews the latest top-rated apps, compares free vs. premium tools, and answers pressing security questions to help you stay ahead of hackers.
Protecting Your Gmail Account
Limit “Summarize” Usage: Use Gemini’s summary feature sparingly for untrusted senders.
Inspect HTML Source: Before summarizing, switch Gmail to “View Original” and search for
<Admin>tags or unusually formatted CSS.Post‑Processing Filters: Configure your email client or a third‑party tool to flag emails containing zero‑font or white‑on‑white text blocks.
Enable Advanced Protection: Turn on Google’s Advanced Protection to require physical security keys for sign‑in, preventing automated credential theft.
User Education: Train teams to verify any urgent security alert via Google Account security settings rather than following prompts in summaries Google Help.
Step-by-Step Guide: How to Create a Gmail Account for Beginners
Key Takeaways
Indirect Prompt Injection exploits AI summaries, embedding invisible phishing instructions.
Gemini’s trust model and raw HTML parsing make it uniquely vulnerable to hidden‑prompt attacks.
Phishing via AI is the next frontier: attackers will target any AI‑driven interface.
Defense requires AI‑aware security: audit hidden markup, limit summary features, and enable physical‑key protections.
User vigilance remains critical: always cross‑check AI alerts with official Google Account security pages.
Are Your Devices Truly Invisible? The Surprising Truth Behind Public vs Private IP Addresses
FAQs
Q: Can I disable hidden‑prompt attacks entirely?
A: Not entirely—but you can reduce risk by limiting AI summaries for unknown senders and using post‑processing filters that detect zero‑size or white‑font HTML blocks.
Q: Are all Gemini users affected?
A: The vulnerability primarily impacts Google Workspace users with the “Summarize this email” feature enabled, but private Gmail users may also see gradual rollouts.
Q: How do I verify if a security alert is genuine?
A: Always check your Google Account’s Security → Recent security events page instead of following prompts in email summaries Google Help.
Q: What long‑term steps should organizations take?
A: Implement AI security audits, integrate AI‑aware threat modeling, and ensure regular red‑teaming exercises include prompt‑injection scenarios.
11 Malicious Google Chrome Extensions You Need to Remove Now
Conclusion
The “Gmail under attack” warning is more than a headline—it’s a call to action. As AI assistants like Gemini become integral to our digital workflows, attackers will innovate, turning helpful features into potent attack vectors. By adopting AI‑aware defenses and staying vigilant against hidden‑prompt scams, you can continue enjoying the productivity benefits of Gemini without sacrificing security.
Ready to secure your inbox? Review Google’s security recommendations, enable Advanced Protection today, and subscribe to SmashingApps for the latest AI security insights.
Now loading...