Click here to buy secure, speedy, and reliable Web hosting, Cloud hosting, Agency hosting, VPS hosting, Website builder, Business email, Reach email marketing at 20% discount from our Gold Partner Hostinger You can also read 12 Top Reasons to Choose Hostinger’s Best Web Hosting
When access to apps or platforms is suddenly restricted, many people react the same way: they search for a workaround. VPN Searches Surge is not just a headline — it’s a behavioral signal that access has been disrupted and users are looking for immediate fixes. This article explains why the search spike matters, the risks it creates, and practical steps readers and organizations can take right now.
3 VPNs That Pass All Tests (2025)
- NordVPN: Zero leaks in tests, RAM-only servers, and Threat Protection to block malware.
- Surfshark: Unlimited devices, Camouflage Mode for bypassing VPN blocks, and CleanWeb ad-blocker.
- ExpressVPN: Trusted Server tech (data wiped on reboot) and consistent streaming access.
Why this spike is happening — the data and the human story
Search and sign-up tracking from industry observers consistently shows the same pattern: when platforms are blocked or when new rules change access, interest in VPNs spikes within hours. People don’t usually adopt VPNs months in advance; they search when they need them. That makes search-volume data a near-real-time proxy for friction in internet access.
UK VPN Ban Explained: What You Really Need to Know About the Online Safety Act
Two consistent findings emerge:
- Searches are an instant indicator of need. When a block occurs, search volume jumps faster than other metrics, because users look for how to reconnect immediately.
- The triggers vary. Spikes follow political restrictions, protest-driven blocks, platform enforcement actions, and new regulations — each driving users toward the same set of circumvention tools.
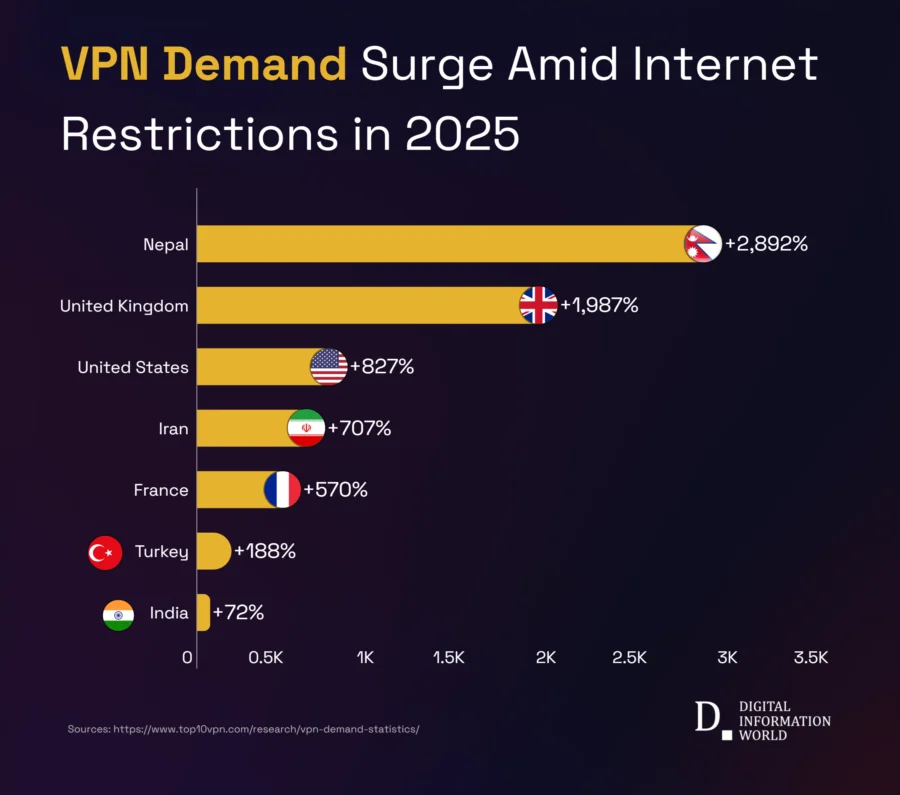
Image Courtesy : © Digital Information World
Three representative cases that show the pattern
Nepal — social platforms as lifelines. When multiple social platforms were blocked, VPN searches surged dramatically in one day. For many Nepalis these services are essential for remittances, emergency alerts, and work; losing access created immediate economic and safety concerns and pushed people to circumvention tools.
United Kingdom — regulation creates curiosity. Announcements of stricter age verification and content controls drove a noticeable uptick in UK VPN searches. This shows that even non-political regulations can trigger the same behavior as outright blocks.
United States — platform enforcement and short but intense bursts. Temporary account suspensions, moderation crackdowns, or threats to remove popular apps lead to short-lived but large spikes in VPN queries and related downloads — enough to move app-store charts and to strain free-tier VPN services.
7 Best Antivirus with VPN to Protect from Malware and Privacy Threats
Why the pattern matters beyond the headline
1) Resilience for critical communications. Mass adoption of VPNs during spikes fragments local information ecosystems. Emergency services, aid organizations, and journalists need contingency channels because IP-level blocks can follow.
2) Privacy and security trade-offs increase. Not all VPNs are equal. Sudden demand pushes users toward free or unfamiliar clients that may log traffic, inject ads, or sell data. A knee-jerk choice can turn a privacy fix into a new privacy problem.
3) Policy and technical responses lag. Governments and platforms design restrictions to control access but underestimate user adaptability. That creates a cycle: blocks → circumvention → new controls → more circumvention. Understanding this dynamic is essential for policymakers who want to limit harm while avoiding unintended consequences.
We have a Free Password Generator Tool that is lightweight, web-based utility that allows users to create strong, secure, and random passwords instantly. This tool is fast, responsive, and easy to use. It’s designed to help individuals, developers, and businesses generate passwords that meet modern security standards, ensuring protection against cyber threats.
New perspectives most coverage misses
Most reporting focuses on raw percentage jumps. Here are three less-covered but important implications:
- Operational readiness matters for civil society. NGOs, local newsrooms, and embassies should preposition secure communication plans — vetted VPN recommendations, offline setup packages, and alternatives like mesh or satellite messaging — because search spikes are early warning signs of worsening restrictions.
- App stores and CDNs are the new chokepoints. When demand surges, app stores and content-delivery networks (CDNs) can be used to limit distribution of circumvention apps. Monitoring those channels often provides earlier signals than national-level filtering alone.
- Portable trust signals reduce harm. In crises users pick apps by visibility: top rankings and positive reviews. Trusted intermediaries (embassies, major NGOs, reputable tech publishers) should maintain evergreen pages listing vetted tools and simple verification checks to reduce the chance users install risky alternatives.
Practical guidance for readers — what to do right now
If you’re affected or want to prepare, follow these steps:
- Verify before installing. Don’t rely on the top search result. Use trusted publications, independent audits, and long-running vendor reputations.
- Prefer audited, privacy-first providers. If privacy matters, choose vendors with independent audits and clear business models; avoid obscure free VPN apps that have no transparency.
- Keep an offline emergency kit. Store installation packages, setup notes, and verification hashes on an external drive or an account you can reach even if app stores are unavailable.
- Plan communications in advance. For NGOs, media teams and families: maintain fallback channels (SMS, alternative secure apps, secure email whitelists) and brief trusted contacts on verification steps.
- Businesses: map external access dependencies. If operations depend on specific social or cloud platforms, prepare VPN-friendly support plans and legal guidance to manage compliance risks.
Key Takeaways
- VPN Searches Surge is a practical, near-real-time signal that users are losing access to services.
- Spikes are driven by political blocks and regulatory changes; both produce rapid demand for circumvention tools.
- Rapid demand increases the risk that users will adopt untrustworthy apps or services.
- Civil society and businesses should preposition contingency plans, vetted toolkits, and fallback communications.
- A compact emergency kit (vetted installers, verification steps, fallback messaging plan) greatly reduces harm during access disruptions.
3 VPNs That Pass All Tests in 2025: Unbeatable Security, Speed & Privacy
FAQs (People Also Ask)
Q: Are VPNs legal where searches are spiking?
A: Laws vary widely. In many countries VPNs are legal but using them to break local laws can carry risk. Always check local regulations and choose tools that match your risk tolerance.
Q: Will a VPN always restore access to blocked services?
A: Often, VPNs route traffic through servers in other countries and restore access, but governments can block known VPN IPs or throttle connections. In extreme cases, proxies, Tor, or satellite services may be required.
Q: How can I tell if a VPN is trustworthy?
A: Look for independent audits, a clear no-logs policy, transparent jurisdiction and business model, and a long-standing reputation. Avoid obscure free apps with unclear data practices.
Q: What should organizations do when VPN searches spike?
A: Treat spikes as an operational alert: activate contingency communications, publish vetted toolkits to trusted channels, and avoid broadcasting operational details that could put users at risk.
Conclusion
When the internet tightens, people look for a way out — and VPN Searches Surge is the clearest indicator of that behavior. The pattern is no longer niche: it affects individuals, journalists, NGOs, and businesses. Simple, verifiable contingency planning — vetting providers in advance, keeping offline installers, and publishing trusted guidance — protects people when restrictions hit.
Consult our internal guide “How to Pick the Right VPN for Everyday Use” (SmashingApps) to build a vetted toolkit for your team.
Now loading...






